THE SWEAR CONTENT
Technology You Can Trust When Truth Is on the Line
SWEAR creates proof-of-original as video is captured, anchors it to a permissioned blockchain ledger, and validates it at playback—so teams can trust what they see.
Recognized. Patented. Proven.
SWEAR’s proof-of-original technology is patented, awarded, and trusted across public safety, enterprise, and government environments where authenticity can’t be optional. Our innovations have been recognized for establishing the foundation of digital content integrity.
2024 CIO Award:
Top Video Authenticity Provider
The Challenge We All Face
When You Can’t Prove What’s Real,
Everything Is Contestable
AI-generated video and simple edits now mimic reality with near-perfect precision. Without capture-time proof, even genuine footage can be challenged. Watermarks and detectors offer helpful signals but remain probabilistic or removable. SWEAR establishes source authenticity at the moment of capture and preserves it through every copy, transcode, or replay.
SWEAR at a Glance
What SWEAR Does - and Doesn’t Do
SWEAR creates independent proof-of-original data alongside each recording and anchors that proof to a permissioned, tamper-evident ledger. It never embeds marks into video or stores the media itself. Instead, SWEAR provides a fast, binary validation (authentic / altered) at playback—so users can instantly confirm what’s real.
Works within existing recorders and VMS systems
Produces deterministic yes/no validation results
Preserves privacy-no video, audio, or metadata stored
Proven across critical security, media, and enterprise applications
How It Works Section
Capture → Protect → Validate
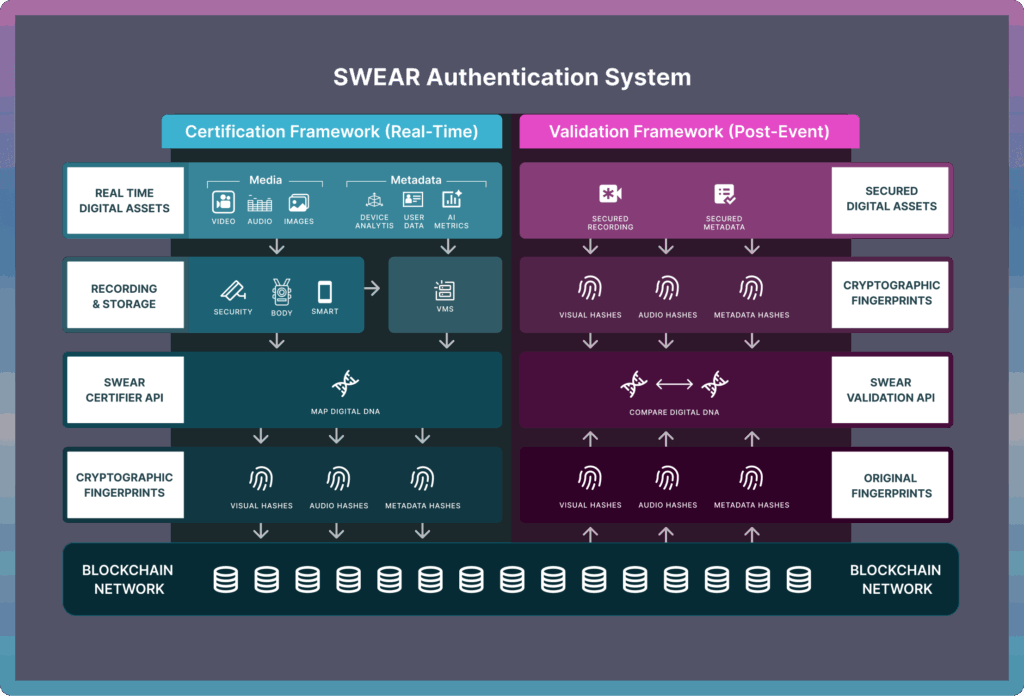
SWEAR protects authenticity at its source. It fingerprints every frame and sound at capture, anchors that proof to a permissioned ledger, and validates the file later at playback—providing cryptographically verifiable trust without altering or storing the media.
Capture Proof-of-Original
Generate Digital DNA (cryptographic fingerprints) for each frame and audio segment in real time.
Anchor to a Tamper-Evident Ledger
Proof and timestamps are written to a tamper-evident blockchain designed for privacy and permanence.
Validate at Playback
SWEAR compares playback content to its original proof, returning a clear pass/fail result and highlighting any mismatch.
Digital DNA ≠ media. SWEAR never embeds, stores, or transmits video or audio.
Architecture Overview
Designed for Proof. Built for Privacy.
SWEAR integrates with existing systems to create a secure chain of authenticity that can be verified anytime.
Runs at the edge or within existing VMS platforms
Supports SaaS, hybrid, or on-prem deployments
Lightweight overhead (<1 MB/hour per stream)
Validates in seconds at playback
Capture ✓
Protect ✓
Validate ✓
Security and Privacy by Design
SWEAR was engineered for high-security environments where data integrity and privacy are non-negotiable.
No media storage: Only proof data (hashes, timestamps, signatures)
Permissioned blockchain ledger ensures tamper-evidence
HSM-backed key governance and audit trails
Privacy-aligned with GDPR and SOC 2 standards
Competitive Landscape
Why SWEAR Solves What Others Can’t
There are many ways to analyze content authenticity, but only one way to prove it. Detectors, labels, and watermarks can signal manipulation, but they remain probabilistic or reversible. SWEAR provides deterministic proof-of-original at the source, built for systems that demand verifiable integrity.
| Capability | SWEAR | AI/Deepfake Detectors | Watermarks & Labels |
|---|---|---|---|
| Proof at Capture (Source Authentication) | ✅ Created the instant content is recorded | ❌ Post-process only | ❌ Added later or inconsistent |
| Deterministic Output (Pass/Fail) | ✅ Binary, cryptographically verifiable | ⚠️ Probabilistic (“likelihood” scores) | ❌ Subject to removal |
| Survives Copies & Transcodes | ✅ Proof remains intact | ⚠️ Confidence drops | ⚠️ Lost on re-encode |
| Privacy Preserving (No Media Stored) | ✅ Only hashes/timestamps stored | ⚠️ May use media samples | ❌ Embeds visible or hidden marks |
| Tamper Evidence (Edit Detection | ✅ Any edit triggers mismatch | ⚠️ Misses partial edits | ⚠️ Cropping/scaling bypass |
| Verifiable at Playback | ✅ Works anywhere | ⚠️ Needs central service | ❌ Depends on watermark presence |
| Evidentiary Confidence | ✅ Deterministic, chain-of-custody ready | ⚠️ Indicative only | ⚠️ Not legally defensible |
| Integrates with Systems (e.g., Milestone) | ✅ SDK + native plug-ins | ⚠️ Limited APIs | ❌ Proprietary |
| Ledger Anchoring | ✅ Permissioned, tamper-evident blockchain | ❌ None | ❌ None |
Detectors analyze. Watermarks label. SWEAR proves.
Built with SHA-3 class cryptographic functions
Anchored to permissioned blockchain (Hyperledger Fabric)
Proof data averages <1 MB/hour per stream
Native Milestone integration for in-player validation
Binary validation completes in seconds at playback
Award-Winning Technology


in both 2024 and 2025 — the security industry’s premier program recognizing innovative products, services, and solutions.

SWEAR’s AI-Proof Video Technology has been recognized as one of TIME’s 2025 Best Inventions. Designed for industries where trust in digital content is critical, SWEAR’s patented technology creates a tamper-proof chain of authenticity that instantly exposes manipulation. As deepfakes and counterfeit media threaten to have great influence, SWEAR delivers an unprecedented safeguard for truth in the digital era.
Proven and Protected Innovation
SWEAR’s patented technology establishes capture-time proof-of-original, ledger anchoring, and deterministic validation. These patents protect the foundation of source authenticity.
| U.S. Patent #10,348,505 | Systems and techniques for validation of trusted media |
| U.S. Patent #10,355,865 | Systems and techniques for certification of trusted media |
| U.S. Patent #10,560,261 | Systems and techniques for capture of trusted media |
| U.S. Patent #10,853,456 | Authenticating media data based on steganographic and blockchain techniques |
| U.S. Patent #11,055,384 | Certifying media data based on steganographic and blockchain |
| U.S. Patent #11,163,855 | Validating media data based on steganographic and blockchain |
| U.S. Patent #11,659,598 | Authenticating media data based upon metadata encoding |
| U.S. Patent #11,683,180 | Protecting digital media with nested hashing techniques |
| U.S. Patent #11,755,693 | Authentication of encrypted media based upon immutable ledger |
| U.S. Patent #11,886,544 | Authentication of compressed media data based upon immutable ledgers |
| U.S. Patent #11,941,090 | Encoding alteration media data within media data |
| U.S. Patent #12,278,856 | Validating media data based on encoded metadata |
| U.S. Patent #12,393,649 | Legder/based validation and re-encoding of digital media |
| Additional patents pending |
Frequently Asked Questions
Here are answers to the most common questions about SWEAR’s video authenticity technology, validation, and deployment.
SWEAR helps security, media, and enterprise teams prove when videos are real. It creates capture-time proof that makes authenticity easy to verify and impossible to fake.
Our patented platform creates a unique, cryptographic fingerprint — what we call Digital DNA — for every frame, pixel, and sound. That fingerprint is then anchored to a blockchain ledger, forming a tamper-evident chain of authenticity designed to persist over time.
The result: video, audio, and images that can be independently validated at any time, by anyone who needs to know the truth.
At a high level, SWEAR operates in three basic steps:
1. Capture: SWEAR fingerprints each frame and sound as a video is recorded.
2. Protect: These fingerprints are stored securely on a blockchain ledger.
3. Validate: The content can later be checked against its proof to confirm authenticity.
This happens automatically and invisibly, without changing how you record or view content.
Instead of detecting AI-generated fakes, SWEAR eliminates doubt by proving what’s real. Anything without a SWEAR proof-of-original is unverifiable. This allows investigators, media teams, and security organizations to dismiss questionable content confidently.
Digital DNA is a unique fingerprint for each video—created as it’s captured, and designed to show if anything changes later.
Unlike traditional metadata or visible watermarks, Digital DNA cannot be forged, copied, or stripped. It provides a tamper-evident record that proves whether a piece of content is genuine or altered.
No. SWEAR never stores or transmits media. Only proof data—fingerprints, timestamps, and signatures—are written to the ledger. This ensures full privacy and compliance with global data protection laws.
If a video has been altered, SWEAR detects it. Any edit breaks the fingerprint match and triggers an authenticity failure at playback. SWEAR’s validation process highlights where mismatches occur, helping teams identify tampering precisely.
SWEAR proof-of-original data remains intact across copies and transcodes. As long as the video’s content structure remains unchanged, authenticity can still be verified.
None. In reference environments, proof-of-original data typically requires less than 1 MB per hour of video on the blockchain. It does not affect the video data.
SWEAR has application in public safety, critical infrastructure, government, media, and enterprise security—environments where video evidence must remain trustworthy and defensible. Our mission is to protect the truth at every lens in the world.
SWEAR connects seamlessly with leading video management systems, including Milestone. It operates as an overlay to existing capture and review workflows—no rip-and-replace required.
SWEAR uses a private, tamper-evident ledger to store proof data. This ensures only authorized participants can write or read entries, supporting compliance and governance in high-security sectors.
Yes. While SWEAR does not directly follow C2PA standards, it complements them by providing mathematical proof of origin that persists even if metadata or credentials are removed.
Yes. SWEAR can operate as a SaaS, hybrid, or fully offline deployment. Proof data can be anchored to a customer-operated ledger if required.
Validation typically completes in seconds during playback, depending on resolution and file size. Results are deterministic and repeatable.
SWEAR ties each proof to a secure timestamp and capture context, making out-of-band manipulations easily detectable. The ledger provides an immutable record of the original file lineage.
Yes. SWEAR’s design is fully aligned with privacy standards. Since no PII or media is stored, data privacy is inherently protected.
Detectors estimate the likelihood of tampering; SWEAR proves the authenticity of source material. It doesn’t predict manipulation—it verifies truth.
Yes, though with limits. Archived videos can be fingerprinted to create proof for future verification, but footage captured before SWEAR integration cannot be proven to its original moment of recording.
SWEAR’s deterministic proof, chain-of-custody audit trail, and ledger anchoring support defensible evidence handling in courts, investigations, and compliance reviews.
Watermarks and labels are visible or embedded signals that can be removed or falsified. SWEAR’s proof-of-original data exists outside the media itself, making it immutable and verifiable even if the video is copied or re-encoded.
For function. The permissioned ledger provides tamper-evidence, auditability, and provenance verification—core requirements for authenticity and compliance.
Yes. The platform is horizontally scalable, supporting high-volume environments such as city-wide surveillance or national broadcast operations.
Any entity responsible for maintaining public trust through digital content: law enforcement, broadcasters, infrastructure operators, and enterprise security teams.
Each proof is cryptographically bound to its original timestamp and device identity. Because the ledger is append-only and tamper-evident, authenticity can be verified years later with the same certainty.
Technology You Can Trust When Truth Is on the Line
SWEAR creates proof that endures—authenticity that can be verified years later and across copies, building digital trust where it matters most.