BLOCKCHAIN-BASED CHAIN-OF-CUSTODY FOR DIGITAL CONTENT
Trust Every Frame
SWEAR gives security leaders confidence in their footage by proving authenticity from the moment of capture through every review, export, and playback. Protect your evidence, your decisions, and your reputation with verifiable proof that cannot be faked.
Recognized. Patented. Proven.
SWEAR’s proof-of-original technology is patented, awarded, and trusted across public safety, enterprise, and government environments where authenticity can’t be optional. Our innovations have been recognized for establishing the foundation of digital content integrity.
2024 CIO Award:
Top Video Authenticity Provider
When Footage Can’t Be Proven, Security Loses Its Foundation
Security systems capture more data than ever, yet AI generated fakes and simple edits make even genuine footage easy to dispute. Without proof established at capture, evidence can be questioned or dismissed. SWEAR creates cryptographic proof of original the moment video is recorded, so authenticity can be confirmed later instantly without moving or exposing sensitive data.
When Footage Can’t Be Proven, Security Loses Its Foundation
Security systems capture more data than ever, yet AI generated fakes and simple edits make even genuine footage easy to dispute. Without proof established at capture, evidence can be questioned or dismissed. SWEAR creates cryptographic proof of original the moment video is recorded, so authenticity can be confirmed later instantly without moving or exposing sensitive data.
Architecture Overview
Built for the Realities of Modern Security
SWEAR fits into existing video management systems and capture workflows, generating proof alongside the video file, not within it. Proof data is encrypted in transit and at rest using industry-standard algorithms (e.g., AES-256 and SHA-256). Ledger access is restricted to authorized roles under defined governance policies, ensuring no single entity can alter or delete proof records.
Immutable proof of original created at capture
Verifiable authenticity across versions and exports
Deterministic pass or fail validation for audit confidence
Privacy preserving, no footage or PII stored
Proven scalability for enterprise security operations
SWEAR is the Solution
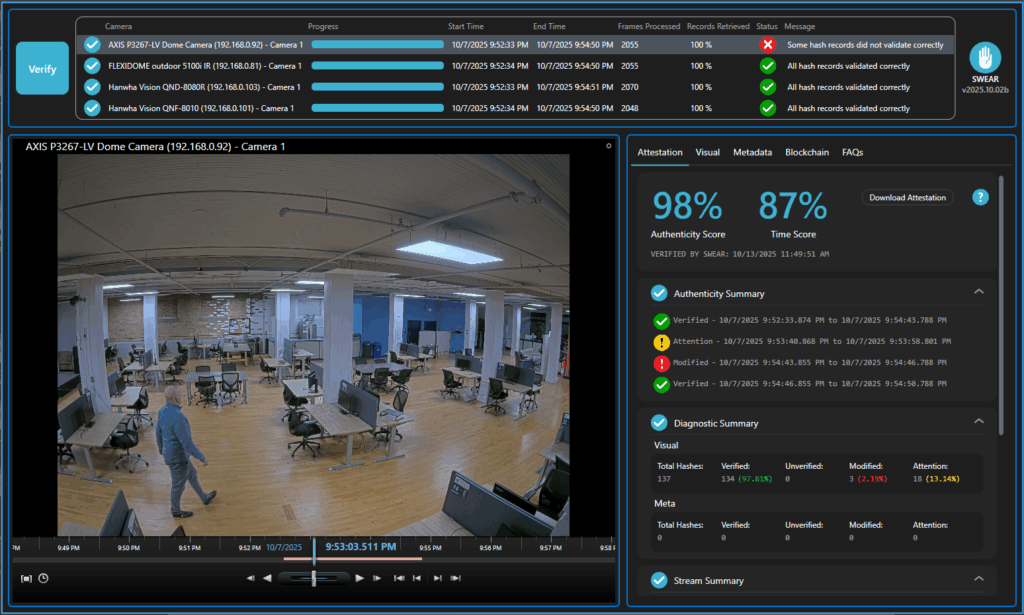
Validate Authenticity Directly Inside Milestone
SWEAR integrates directly with Milestone XProtect, the leading open platform for video management. Operators can verify footage authenticity within the Milestone interface without exports, third party tools, or data movement.
Validation occurs with minimal latency and no performance degradation to Milestone workflows. SWEAR and Milestone communicate through secure, authenticated APIs that maintain strict role-based access controls, ensuring validation events cannot be spoofed or intercepted.
During playback, SWEAR checks the file against its proof of original record and returns a clear validation result in seconds. The validation status appears in the player, giving immediate confidence in every review.
Native Milestone XProtect player-level validation interface
No alteration of media, proof data remains separate
Deterministic pass or fail with secure event logging
Supports case documentation and evidentiary workflows
Ideal for SOCs, law enforcement, and infrastructure operations
Standards, Security & Interoperability
Enterprise-Grade by Design:
Secure, Private, Standards-Aware
SWEAR’s framework is engineered for organizations that must defend data integrity under audit and compliance. Proof data is generated at capture and anchored to a permissioned ledger, while media never leaves the operator’s control.
Each proof event is recorded with full cryptographic lineage and stored under immutable governance. SWEAR’s ledger framework includes access controls, audit logging, and tamper detection designed for security operations centers (SOCs).
Privacy preserving architecture, no media stored or transmitted
Permissioned ledger anchoring for tamper evidence and traceability
Complements C2PA and CAI content credential models with source proof
Aligned with SOC 2 and GDPR principles for regulated environments
Works with existing VMS and evidence systems, no rip and replace
SWEAR integrates with existing SOC and SIEM systems through API and syslog connectors, allowing validation events to be correlated with other security data streams. This enables real-time incident response and audit trail continuity within enterprise monitoring tools.
Where Proof-of-Original Protects the Mission
SWEAR protects the integrity of video data in the most demanding security settings, where compromised footage is not just costly, it is catastrophic.
Public Safety
Preserve evidentiary confidence from capture to courtroom.
Enterprise Security
Verify authenticity across thousands of cameras without disrupting operations.
Critical Infrastructure
Defend against manipulation or misinformation targeting visual records.
Frequently Asked Questions
Here are answers to the most common questions about SWEAR’s video authenticity technology, validation, and deployment.
No. SWEAR never stores or transmits footage. Only cryptographic proof data, fingerprints, timestamps, and signatures are recorded on a permissioned ledger.
Proof data retention follows customer policy and regulatory requirements. SWEAR supports configurable retention schedules and secure deletion mechanisms to meet compliance needs.
SWEAR creates a proof of original at capture and anchors it with a secure timestamp and device context. During playback, validation confirms whether the file still matches that original proof, preserving chain of custody and auditability.
Yes. SWEAR’s platform and deployment architecture have undergone third-party security reviews and penetration testing, ensuring operational resilience and data protection at scale.
SWEAR’s Milestone integration enables authenticity checks within the player. Operators see pass or fail validation results during playback and can log these results as part of their case documentation.
SWEAR does not implement or claim compliance with C2PA. The C2PA standard governs how provenance metadata, or Content Credentials, is signed and shared. SWEAR complements this by providing an independent proof of original at capture that remains verifiable even if credentials are unavailable or removed.
SWEAR does not classify media as real or fake. It proves when video is authentic to its original capture. Files without a SWEAR proof are simply unverifiable.
Copies and transcodes that preserve the content structure can still be validated against the original proof. Any change triggers a validation failure.
Each proof includes secure capture context, such as device ID and timestamp, allowing detection of out of band manipulation or relabeling attempts.
Watermarks and labels can be removed or forged. SWEAR’s proof exists outside the media and is anchored to a tamper evident ledger, enabling verification even if metadata is stripped or the file is copied.
Archived footage can be fingerprinted to create future validation proofs, though only footage captured with SWEAR active can be verified to its moment of origin.
SWEAR processes only cryptographic proof data, never the footage itself. This ensures privacy compliance even in regulated or public spaces.
To learn more or request access, contact us.
Technology You Can Trust When Truth Is on the Line
SWEAR creates proof that endures—authenticity that can be verified years later and across copies, building digital trust where it matters most.