Validate, don’t speculate.
Turn Smartphones into AI Resistant Video Cameras
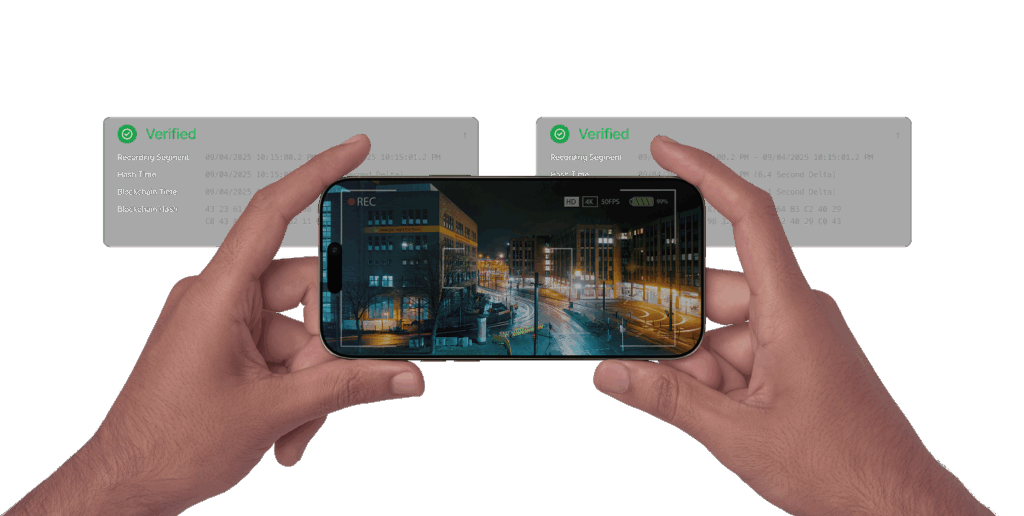
Anyone can record video. Almost no one can prove, with certainty, that what they are showing is the untouched original moment. SWEAR gives mobile devices the ability to generate proof of original at the moment of capture so that every frame can be verified later. If it was captured on a SWEAR enabled device, you can prove it.
Opportunity
Billions of Cameras.
Zero Proof.
Nearly nine billion phones capture video that becomes evidence, news, policy, claims, payouts, arrests, and headlines. But today, almost none of that footage can stand on its own without being challenged.
Deepfakes and AI generated clips are everywhere. Cheap editing tools can rewrite reality in seconds. Phones are still treated as “good enough capture devices,” not as sources of defensible truth.
This is the gap. SWEAR closes it.
Works at the OS layer, the firmware layer, or the application layer
Collects rich capture context from the device at the moment of recording
Creates independent proof that sits alongside the file, not inside the file
Anchors authenticity to a permissioned ledger for future verification
Scales from a single camera app to an entire device portfolio
SWEAR gives mobile and embedded devices the ability to create verifiable proof of original when the video is captured. That proof travels with the content everywhere it goes and can be checked at any time in the future. If the proof holds, the video is authentic. If it breaks, something in the chain has been altered. It is that simple, and that hard to fake.
Why It Matters
Your Footage Will Be Challenged.
Will You Be Able to Defend It?
If you build cameras, capture platforms, field applications, content tools, safety tools, evidence tools, or social platforms, you already know the question that is coming: “How do you know this video is real.”
That question is now appearing in:
Courtrooms
Claim Reviews
Compliance Audits
Newsrooms
Internal Investigations
National Security Briefings
If you cannot answer with certainty, you have risk. Legal risk. Brand risk. Safety risk.
SWEAR gives you a way to answer with certainty.
By establishing proof of original at capture, SWEAR allows your organization say: this was recorded on this device, at this time, under these conditions, and it has not been altered since. That level of confidence is now required. It is quickly becoming the expectation for serious platforms, serious devices, and serious institutions.
Proof at Capture. Confidence for Life.
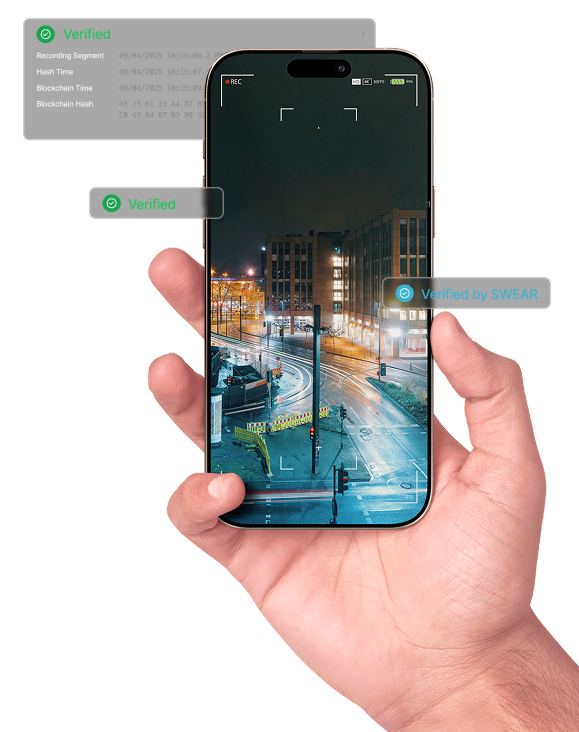
SWEAR does not try to guess whether a video is fake after the fact. It locks in truth at the source. The system establishes proof of original the instant a video is captured and makes that proof independently checkable anywhere that video is later viewed or used. The model is simple and consistent across SWEAR: Capture. Protect. Validate.
Capture
The device records video as usual. SWEAR runs beside the camera pipeline, collecting sensor ID, time, location, motion, and other context to describe when and how footage was created. It instantly creates proof of original for that recording.
Protect
SWEAR safeguards that proof so it can’t be altered. It generates a cryptographic fingerprint of the captured data and anchors it to a permissioned ledger managed by the OEM or customer. The video never leaves the device, ensuring a secure chain of custody from capture onward.
Validate
Later—during review, claims, or publication—SWEAR re-fingerprints the file and checks it against the protected proof. The result is simple: pass or fail. Either the footage matches its original state or it doesn’t. No watermark. No overlay. Just proof.
SWEAR avoids fragile watermarks or metadata tags. There is only proof.
Built to Live Inside Every Device
Native. Private. Defensible.
SWEAR is not a filter. It is not a label. It is not a watermark. It is an authenticity layer designed to live inside devices, operating systems, chipsets, and high value capture applications.
You can integrate SWEAR in three ways, depending on how deep you own the stack:
OEM and OS Partners:
integrate SWEAR at the firmware or OS layer to make proof of original a standard capability of the camera pipeline. This turns every shipped device into an AI resistant capture device.
Chipset and Silicon Partners:
embed SWEAR as part of secure capture paths so that proof begins at the sensor and is carried forward through the image signal processor and into storage. This places authenticity where it is hardest to fake.
Application and Platform Teams:
use SWEAR SDKs and APIs to bring proof of original capture into your mobile app, field app, reporting tool, inspection tool, or publishing pipeline. This is ideal for sectors like journalism, insurance, safety, compliance, and high stakes UGC.
In every case, SWEAR is designed for:
Minimal Overhead
Privacy Preservation
No Exposure Of The Underlying Video
No Change To The User’s Capture Flow
What This Unlocks
Build Products That Can Withstand Scrutiny
The value is not just protecting the video. The value is protecting you.
When you ship devices, apps, or platforms that can prove authenticity, you unlock:
Defensible evidence:
Content that stands up in legal, regulatory, and internal review settings because it can be validated, not argued
Trusted reporting:
Footage from the field that can be cleared faster, published faster, escalated faster, because its origin can be proven without guesswork.
Fraud reduction:
Claims, inspections, and documentation that can be tied to specific capture events and cannot be quietly manipulated.
Platform integrity:
Ability to distinguish what was really captured from what was generated or altered, and act on it.
Brand credibility:
Your device, your app, or your network becomes known for truth, not noise. That matters more every single day.
Defensible evidence:
Content that stands up in legal, regulatory, and internal review settings because it can be validated, not argued
Trusted reporting:
Footage from the field that can be cleared faster, published faster, escalated faster, because its origin can be proven without guesswork.
Fraud reduction:
Claims, inspections, and documentation that can be tied to specific capture events and cannot be quietly manipulated.
Platform integrity:
Ability to distinguish what was really captured from what was generated or altered, and act on it.
Brand credibility:
Your device, your app, or your network becomes known for truth, not noise. That matters more every single day.
How It Works Section
High Stakes Capture Demands High Confidence
Some industries cannot afford “probably real.” SWEAR supports use cases where trust in mobile video is now a frontline requirement.
Public Safety and Investigation
Field footage must stand up in internal review and, when required, in court. SWEAR helps preserve evidentiary confidence from the first moment of capture.
Insurance, Warranty, and Remote Inspection
Payouts and decisions depend on what was shown. SWEAR lets you confirm that inspection footage is authentic and tied to a real capture event.
News and Media
Newsrooms need to verify source truth before publishing. SWEAR supports source credibility without exposing the underlying footage to third parties.
Critical Infrastructure and Industrial Operations
Incident video from inside restricted environments cannot be tampered with if safety, liability, or reporting are on the line.
Social and User Generated Content
Platforms must separate real human capture from synthetic, AI generated media. SWEAR provides a simple, defensible authenticity signal without revealing private content.
Frequently Asked Questions
This FAQ answers the most common questions asked by platform owners, OEMs, chipset manufacturers, application developers, and security leaders who are evaluating SWEAR for mobile deployment. It provides both high-level clarity and deep technical detail on how SWEAR establishes, protects, and validates proof of original for mobile video capture.
The rise of AI-generated and manipulated video has made it nearly impossible to trust what we see. SWEAR solves this problem by allowing any mobile device to prove what’s real. It transforms smartphones into AI-resistant video cameras, creating cryptographically verifiable proof of original at the moment of capture so that every recording can later be validated as authentic. This ensures that mobile-captured content can serve as reliable evidence, documentation, or record across security, enterprise, media, and consumer ecosystems.
SWEAR operates alongside the camera pipeline, not inside the file. During capture, it collects trusted metadata such as sensor ID, device signature, location, timestamp, and motion state. It uses this information—together with frame- and audio-level data—to generate a cryptographic fingerprint of the recording. That fingerprint is then anchored to a permissioned blockchain ledger, producing an immutable proof-of-original record. When the file is later reviewed, SWEAR re-fingerprints the video and performs a deterministic comparison that returns a binary result: Authentic or Not Authentic.
No. SWEAR never embeds anything into the video or changes the file in any way. The media remains pristine and unmodified. SWEAR generates and stores a separate proof record—consisting of hashes and metadata—cryptographically linked to the video. This means no visible watermark, no invisible tag, and no impact on playback or file compatibility. SWEAR’s proof exists independently, making it tamper-evident yet fully privacy-preserving.
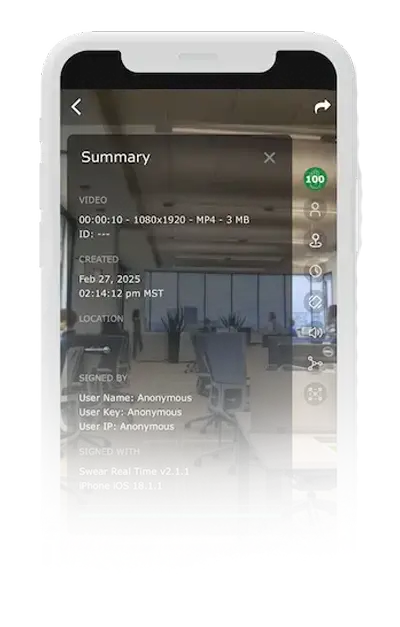
Proof of original is digital evidence that a piece of content is genuine. It’s created automatically at the time of capture and includes:
- Cryptographic fingerprints derived from the video and audio streams
- Contextual metadata from the device (time, location, sensor ID, etc.)
- Secure digital signatures and timestamps
These elements combine to make each recording uniquely verifiable forever. When re-validated, the proof confirms whether the content remains intact or has been modified in any way.
SWEAR can collect and process over one hundred data signals from a device at capture, including sensor IDs, time, location, motion, ambient light, orientation, and network conditions. These signals are fused with hashes of the video and audio data to produce a set of cryptographic fingerprints. Each fingerprint is digitally signed, time-bound, and anchored to a permissioned blockchain ledger managed by the OEM or enterprise partner.
This architecture ensures:
- The proof cannot be silently modified or deleted
- The video file itself is never transmitted or exposed
- The relationship between the proof and the original capture remains mathematically verifiable indefinitely
When validation is requested—whether minutes or years later—SWEAR re-fingerprints the video file and compares that result to the original proof in the ledger. If they match, the video is confirmed Authentic; if not, the validation returns Not Authentic. This pass/fail output removes interpretation and subjectivity, delivering a simple, defensible answer suitable for legal, regulatory, or journalistic contexts.
Detection tools and watermarking schemes work after the fact. They attempt to infer or signal whether something might be synthetic. SWEAR works before manipulation is possible—at the moment of capture.
- AI detection = probabilistic guesswork after creation
- Watermarks = visible or invisible markers that can be stripped or spoofed
- SWEAR = cryptographic proof anchored at capture, impossible to fake or remove
This proactive model prevents disputes rather than analyzing them later.
SWEAR is designed for offline-first reliability. When a device lacks connectivity, proofs are generated and securely stored locally. Once a connection is re-established, the proofs are anchored to the ledger automatically. Each includes a trusted timestamp, maintaining full provenance and a complete chain of custody even when recorded in disconnected or air-gapped environments.
No. SWEAR never transmits or stores the actual video, nor does it collect personal user data. Only non-visual, non-personal metadata and derived hashes are processed. The proof is designed to protect privacy while preserving verifiability. This allows deployment in privacy-critical domains such as law enforcement, healthcare, national security, and enterprise compliance.
SWEAR is engineered for real-time efficiency. Proof data is extremely small—typically only a few megabytes per hour of video—making it suitable for continuous mobile operation without affecting capture speed, device storage, or battery performance. This lightweight design enables large-scale OEM deployments across billions of handsets.
SWEAR is flexible and modular. It can be deployed at three levels of integration:
- Chipset / Silicon: embedded inside secure enclaves or trusted execution environments for root-of-trust authenticity
- OS / Firmware: integrated directly into the camera pipeline to make proof of original a standard capture feature
- Application / SDK: implemented through SWEAR’s SDKs or APIs for field, reporting, or inspection apps
This layered approach lets OEMs, platform providers, and app developers choose the depth that matches their control of the hardware or software stack.
SWEAR uses permissioned blockchain technology—often Hyperledger Fabric—to record and manage proofs. This model enables each OEM, platform, or enterprise to host its own ledger instance, maintaining full sovereignty and compliance while benefiting from immutable audit trails. The ledger stores proof data only; no video content ever resides on-chain.
Any alteration—whether a single frame edit, color correction, audio change, or recompression—breaks the mathematical relationship between the video and its proof. Validation immediately fails, signaling that the file no longer matches its original capture. SWEAR makes tampering not just detectable, but provable.
SWEAR does not directly implement or comply with the C2PA standard, but it complements it. C2PA establishes transparency about content after creation through credentials and labeling. SWEAR provides verifiable proof at capture, before any editing or transmission occurs. Together, these approaches create a complete provenance chain—from point of origin to point of display.
Yes. SWEAR integrates with industry-leading VMS platforms like Milestone XProtect, allowing authenticity validation directly within the playback interface. This eliminates the need for file exports or external verification tools and maintains a closed, secure chain of custody for video evidence.
SWEAR is gaining adoption in sectors where video authenticity is mission-critical:
- Security and Public Safety: body-worn and surveillance video validation
- Insurance and Warranty: remote inspection and fraud prevention
- Media and Journalism: source verification and content authentication
- Industrial Operations: safety audits and compliance recording
- User-Generated Content Platforms: distinguishing genuine human capture from synthetic media
Yes. SWEAR’s architecture is inherently distributed and horizontally scalable. Proof generation can be parallelized across capture hardware and synchronized with regional or global ledger instances. This enables deployment across entire OEM fleets, telecom networks, and developer ecosystems.
Watermarks can be stripped, signatures can be copied, and AI detection can be deceived. SWEAR’s proof-of-original is cryptographically linked but physically separate from the media. It cannot be forged, transferred, or removed. This independence gives it evidentiary weight and technical resilience unmatched by traditional approaches.
Begin by requesting a Developer Brief or accessing the SWEAR SDK Portal. SWEAR’s integration team will help identify where proof generation belongs in your capture architecture—chipset, OS, or application—and assist with sandbox testing, performance validation, and compliance verification.
AI-generated video and synthetic media are eroding public trust in visual evidence. SWEAR provides the missing infrastructure to prove truth at capture—ensuring that mobile recordings used in journalism, law, safety, and commerce can be trusted without debate. It’s not about analyzing fakes later; it’s about preventing doubt from the start.